SSO (Single Sign-On) : SSO ID, SSO login, SSO ID Login & SSO Registration
SSO (Single Sign-On) is an authentication scheme that allows users to log in with a single ID and password to access multiple applications or services.
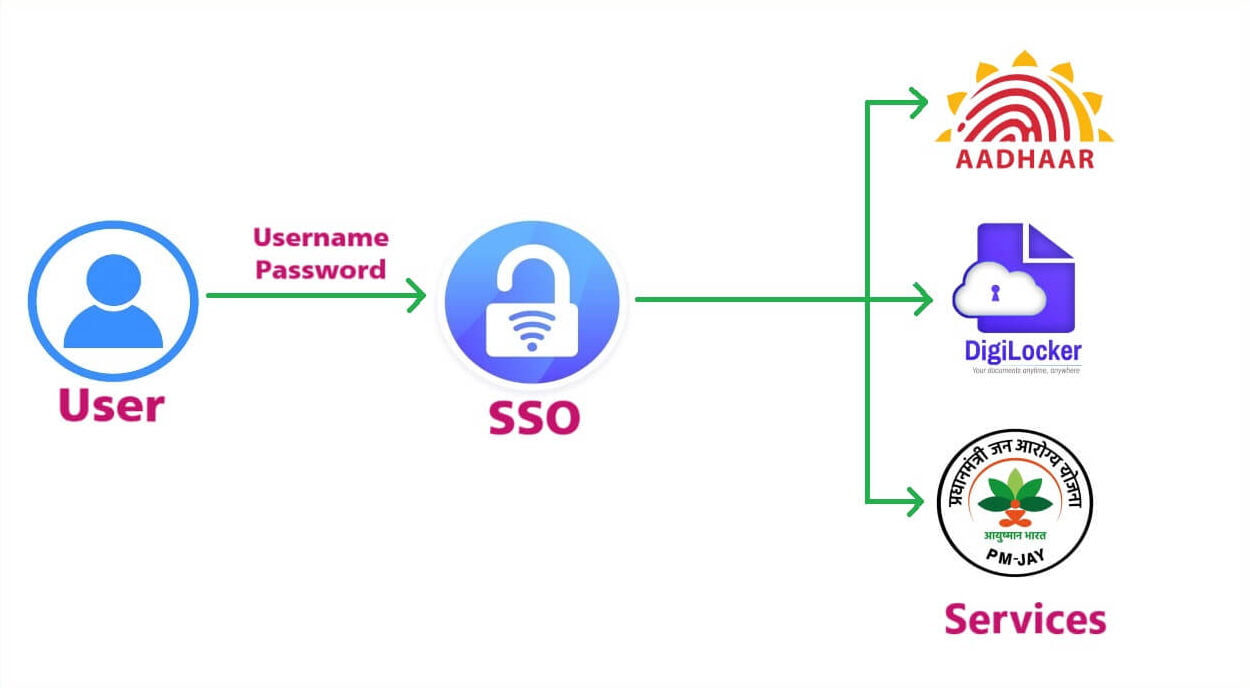
SSO : Overview
| Authentication | Verifies user credentials and establishes identity. |
| Authorization | Determines access rights to resources. |
| Attributes Exchange | Shares user data across systems to avoid duplication. |
| User Management | Administers user accounts across domains. |
| Session Sharing | Allows session information to be used across different domains. |
| Security Policy | Enforces policies like the same-origin policy for data integrity. |
| Protocols | Defines how SSO shares session information across domains. |
| Advantages for Users | Reduces password fatigue, mitigates risk of password access by third parties. |
| Advantages for Businesses | Increases customer satisfaction, reduces IT costs for password management. |
| Disadvantages | Heightens risk if credentials are compromised, as access is granted to multiple resources. |

What is SSO ?
SSO is designed to minimize the number of times a user needs to enter their login credentials when switching between applications that are within the same trust network. This means that after the initial login, the user can navigate between different systems or services without the need to log in again for each one.
SSO is designed to streamline the user experience by reducing the number of times users must enter their credentials, thereby enhancing productivity and reducing the risk of password fatigue. The technology works by establishing a trusted relationship between the service provider (the application requiring authentication) and the identity provider (the system which verifies the user’s identity).
SSO is widely used in enterprise environments as it simplifies the management of user access across various platforms and applications. It also improves security by centralizing the authentication process, allowing for better monitoring and potential threat detection. Moreover, with Single Sign-On, users are encouraged to maintain stronger passwords, as they need to remember only one set of credentials, reducing the likelihood of using weak or repeated passwords across multiple accounts.
How Does SSO Work ?
SSO works by combining different components to create a smooth authentication experience:
1. The User: The individual who wants to access multiple applications.
2. The Identity Provider (IdP): The service that maintains and verifies the user’s identity.
3. The Service Provider (SP): The application or service the user wants to access.
4. The User Agent: The interface used by the user, typically a web browser.
Here is a detailed explanation of the process of SSO :
- Step 1: Initial Login – The user tries to get access to a service or an application (Service Provider). If they are not already authenticated, the service redirects the user to the Identity Provider.
- Step 2: Authentication – The Identity Provider verifies the user’s identity. This can be done through various methods such as a password, bio metrics, or multi-factor authentication. If the user has already authenticated earlier, this step may be skipped due to existing session cookies.
- Step 3: Assertion Generation – Once authenticated, the Identity Provider generates an assertion, which is a token or a piece of information that contains the user’s identity details and possibly other attributes. This assertion is securely transmitted to the Service Provider.
- Step 4: Access Granted – The Service Provider verifies the assertion from the Identity Provider and, if it trusts the assertion, grants access to the user.
- Step 5: Subsequent Accesses – When the user attempts to access another service or application that is part of the Single Sign-On framework, the process from step 2 onward is typically streamlined. Since the user is already authenticated with the Identity Provider, they are quickly granted access without needing to re-enter their credentials.
Benefits of SSO
- Centralized Authentication – SSO allows users to access multiple applications with one set of login credentials.
- Enhanced User Experience – With SSO, users no longer need to remember multiple usernames and passwords, simplifying the login process and improving overall user satisfaction.
- Increased Productivity – Users save time by avoiding multiple login prompts, which can significantly increase productivity as they can access necessary applications faster.
- Reduced Password Fatigue – By minimizing the number of passwords users must remember, SSO reduces the risk of password fatigue, leading to stronger adherence to security practices.
- Lower IT Support Costs – Single Sign-On reduces the number of password reset requests and other login-related support issues, thus lowering the overall IT support costs.
- Improved Security and Compliance – Centralized management of user access makes it easier to enforce security policies and ensures compliance with regulatory requirements.
- Streamlined User Management – IT administrators can manage user access to multiple systems from a single interface, streamlining the user management process.
- Reduced Risk of Phishing Attacks – With fewer login prompts, the potential for phishing attacks is reduced as users become accustomed to logging in once and are less likely to enter credentials into fraudulent sites.
- Enhanced Reporting and Monitoring – Centralized authentication enables better tracking of user activities across applications, facilitating enhanced reporting and monitoring for security purposes.
Implementing SSO in India
SSO (Single Sign-On) solutions have become a cornerstone of efficient and secure user authentication processes around the world. In India, with its rapidly growing digital landscape, the implementation of SSO systems is more relevant than ever. This website aims to provide a comprehensive guide to businesses in India looking to implement Single Sign-On, ensuring a seamless user experience while maintaining high security standards.
The Benefits of SSO in India
India’s diverse and expansive digital ecosystem presents unique challenges and opportunities. The implementation of SSO can offer multiple benefits :
– Enhanced User Experience: Users can navigate between services without repeatedly entering login credentials.
-Improved Security: Reduces the chances of password-related breaches.
– Increased Productivity: Saves time for users and IT departments by streamlining the login process.
– Compliance Support: Helps in adhering to various Indian regulatory requirements regarding data protection and privacy.
- Step 1: Assessing Your Needs
The first step to implementing SSO is to assess your organization’s specific needs. Consider the following :
– The number and nature of applications your users need access to.
– Compliance requirements specific to your industry and the Indian market.
– The existing IT infrastructure and its compatibility with Single Sign-On solutions.
- Step 2: Choosing the Right SSO Solution
There are various SSO solutions available, each with its features and capabilities. When choosing an Single Sign-On provider, consider:
– Compatibility with your current infrastructure.
– Support for protocols like SAML, Open ID Connect, and OAuth.
– The provider’s track record and reputation in the Indian market.
- Step 3: Planning the Implementation
Once you have chosen an SSO solution, detailed planning is essential. This includes:
– Defining a clear implementation timeline.
– Identifying the applications that will be integrated first.
– Planning for user training and support.
- Step 4: Executing the Implementation
With a plan in place, you can begin the implementation process. This typically involves:
– Setting up the Single Sign-On infrastructure.
– Integrating applications with the Single Sign-On system.
– Testing for functionality and security.
- Step 5: User Education and Support
For an Single Sign-On system to be successful, users must be comfortable using it. Provide comprehensive training and resources, such as:
– User manuals and FAQs.
– Training sessions or webinars.
– A dedicated help desk for user inquiries.
- Step 6: Ongoing Management and Review
After implementation, ongoing management is critical. This includes:
– Monitoring system performance and user feedback.
– Regularly reviewing security protocols.
Challenges and Considerations
While implementing SSO in India, businesses may face challenges such as :
- Ensuring compatibility across diverse systems and applications.
- Addressing concerns around data privacy and compliance with Indian laws like the Personal Data Protection Bill.
- Managing user resistance to change.
To mitigate these challenges, it is important to maintain open communication with all stakeholders, invest in robust security measures, and stay informed about regulatory changes.
Conclusion
Implementing SSO (Single Sign-On) in India can bring significant benefits to organizations by enhancing user experience, bolstering security, and streamlining access to multiple applications. By following a structured approach—from assessing needs to ongoing management—businesses can ensure a smooth transition to an Single Sign-On system. As India continues to advance its digital infrastructure, adopting technologies like SSO will be crucial in staying competitive and secure in the digital age.
SSO : Challenges and Key Considerations
In the modern digital landscape, where users must remember credentials for countless applications and services, SSO (Single Sign-On) has emerged as a beacon of convenience and security. Single Sign-On allows users to access multiple applications with a single set of credentials, streamlining the authentication process and enhancing user experience.
Nonetheless, there are challenges that come with implementing SSO. Organizations must navigate a complex array of considerations to ensure that their Single Sign-On solution is secure, efficient, and meets the needs of all stakeholders. In this blog post, we will explore some of the most pressing challenges and considerations when adopting an Single Sign-On solution.
Challenges of SSO Implementation :
1. Security Concerns: One of the most significant challenges of SSO is maintaining a high level of security. While SSO can reduce the number of attack vectors by minimizing password fatigue and the risk of weak credentials, it also creates a single point of failure. If an attacker compromises the Single Sign-On credentials, they gain access to all linked applications. Therefore, implementing robust security measures, such as multi-factor authentication (MFA) and regular security audits, is crucial.
2. Integration with Existing Systems: Integrating SSO with an organization’s existing infrastructure can be complex, particularly if there are legacy systems or a variety of cloud and on-premises applications. Ensuring compatibility and seamless integration requires thorough planning and often customization, which can be resource-intensive.
3. User Experience: While SSO is intended to enhance user experience by simplifying access to services, poorly implemented SSO can lead to confusion and frustration. Users may encounter issues with session timeouts, login failures, or difficulty accessing certain applications. It’s essential to design an SSO system that is intuitive and user-friendly.
4. Compliance and Privacy Regulations: Organizations must ensure that their SSO solution complies with relevant data protection and privacy regulations such as GDPR, HIPAA, or CCPA. This involves securing user data and providing transparency about how it’s used and stored.
5. Vendor Lock-In: Choosing an SSO provider often means committing to their ecosystem. Organizations must consider the implications of vendor lock-in, such as limited flexibility and potential difficulties if they decide to switch providers in the future.
Key Considerations for a Successful SSO Strategy :
1. Assessing Organizational Needs: Before implementing an SSO solution, it’s essential to understand the specific needs of your organization. This includes identifying the applications that require Single Sign-On integration, understanding user roles and permissions, and determining the level of security needed.
2. Choosing the Right SSO Solution: There are many SSO solutions available, each with its own set of features and capabilities. Organizations should conduct thorough research to select a solution that aligns with their security requirements, budget constraints, and scalability needs.
3. User Education and Training: To ensure successful adoption of the SSO system, organizations must invest in user education and training. Users should understand how to use the Single Sign-On system effectively and be aware of any changes to their login processes.
4. Continuous Monitoring and Improvement: An SSO solution should not be static. It requires ongoing monitoring to detect potential security threats and performance issues. Regularly reviewing and updating the SSO implementation can help maintain its effectiveness over time.
5. Developing a Contingency Plan: Organizations must have a contingency plan in place for situations where the SSO system is unavailable or compromised. This plan should include steps for quickly restoring access to critical applications without compromising security.
The Adoption of SSO by Indian States, Dept. and Ministries
In India, various states, Dept. and ministries are recognizing the benefits of SSO and are implementing it to enhance their digital infrastructure. We will explore how Indian states and ministries are using SSO to improve service delivery and data security.
1. Rajasthan: The state of Rajasthan has implemented an SSO Rajasthan portal that provides citizens with access to a wide range of government services. From filing taxes to applying for scholarships, the Single Sign-On portal acts as a one-stop-shop for residents, improving the efficiency of service delivery.
2. Karnataka: The Karnataka government has also embraced SSO Karnataka through its e-Governance department, providing a unified platform for accessing various government services. It simplifies processes for businesses and individual alike, promoting transparency and ease of use.
3. MeriPehchaan NSSO: MeriPehchaan NSSO is a digital identity authentication solution developed to streamline the process of accessing multiple services with a single set of credentials. It is designed to serve as a one-stop authentication gateway for Indian citizens to log in to various government and private sector services without the need to maintain numerous usernames and passwords.
4. Sikkim: In Sikkim, the state government has implemented an SSO Sikkim portal to facilitate easy and secure access to various government services. This guide will walk you through the steps to use Single Sign-On Sikkim, ensuring a smooth and hassle-free experience.
SSO Conclusion
In conclusion, SSO (Single Sign-On) is a user authentication process that allows a user to access multiple applications with one set of login credentials, thereby streamlining the sign-in process and enhancing user experience. Single Sign-On solutions offer numerous benefits, including improved security by reducing password fatigue, increased productivity as users no longer need to remember multiple passwords, and reduced IT costs related to password recovery and help desk support. Implementing an SSO system can also provide valuable insights into user activity, aiding in compliance and auditing processes.
However, organizations must carefully consider the security implications of centralizing access to various systems and ensure robust protocols are in place to prevent unauthorized access. The selection of an Single Sign-On provider should be done with due diligence, taking into account the compatibility with current systems, scalability, and compliance with industry standards.
With the right implementation, Single Sign-On can provide a secure and efficient way of managing user access across an enterprise’s suite of applications and services. It is a critical component in modern IT environments, facilitating seamless and secure user access while supporting the overall security posture of the organization.
SSO FAQs
1. What is SSO (Single Sign-On) ?
Single Sign-On is an authentication scheme that allows users to log in with a single ID and password to access multiple applications or services. It is designed to minimize the number of times a user needs to enter their login credentials when switching between applications that are within the same trust network.
2. How does SSO improve security?
Single Sign-On can improve security by reducing the number of attack surfaces since users only have to manage one set of credentials. This minimizes the likelihood of password fatigue, which can lead to weak password creation. Additionally, solutions often come with centralized monitoring and management, which allows for quick response to suspicious activities or potential breaches.
3. Does SSO save time for users?
Yes, it can save time for users by streamlining the login process. Users do not have to repeatedly enter credentials for different services, which reduces the overall time spent logging in and can increase productivity.
4. Is SSO the same as password synchronization?
No, Single Sign-On is not the same as password synchronization. Password synchronization involves having the same password across multiple systems, but users still need to log in to each system separately.
5. Can SSO work across different domains?
Yes, It can work across different domains using federated identity management. Protocols like Security Assertion Markup Language (SAML), OpenID Connect, and OAuth are often used to enable secure cross-domain authentication.
6. What happens if an SSO system fails?
If an Single Sign-On system fails, it may prevent users from accessing any of the connected applications until the issue is resolved. This is why it’s important to have a robust disaster recovery plan and backup authentication methods in place.
7. How do I choose an SSO solution for my organization?
When choosing an SSO solution, consider factors such as compatibility with your existing systems, security features, ease of deployment and management, user experience, and compliance with industry standards. It’s also wise to evaluate the vendor’s reputation and support offerings.
8. How does SSO handle user logout?
Single Sign-On handles user logout by terminating the user session and ensuring that all linked applications also end their sessions. This process should be secure and complete to maintain the integrity of the user’s security posture.
9. What are some common SSO protocols?
Some common Single Sign-On protocols include:
– Security Assertion Markup Language (SAML)
– OpenID Connect
– OAuth 2.0
These protocols provide frameworks for exchanging authentication and authorization data between parties.